Criminal trial status and defense points of providing others with spying software
On November 14, 2021, the National Network Information Office issued the "Regulations on the Administration of Network Data Security (Draft for Comments)" and publicly solicited opinions from the public. This regulation aims to implement the provisions of laws such as the "Network Security Law of the People's Republic of China", "Data Security Law of the People's Republic of China", and "Personal Information Protection Law of the People's Republic of China" on data security management, regulate network data processing activities, protect the legitimate rights and interests of individuals and organizations in cyberspace, and maintain national security and public interests. The draft clearly stipulates that individuals and organizations are not allowed to provide other people with flipping software, but it does not prohibit individuals from using flipping software. However, there are still cases where individuals and organizations are subject to administrative penalties due to the use of flipping software.
In view of this, on the occasion of the first anniversary of the publication of the draft for comment, the author believes that it is necessary to conduct a review of the judicial practice of individuals and organizations using and providing other people with flipping software, and at the same time try to find out the reasons for this type of case as much as possible.
1、 Individuals and organizations may be subject to administrative penalties if they use the software
Article 6 of the Provisional Regulations of the People's Republic of China on the Administration of International Networking of Computer Information Networks (Revised in 1997) and Article 7 of the Implementation Measures both stipulate that computer information networks must use the international entrance and exit channels provided by the national public telecommunications network of the Ministry of Posts and Telecommunications for direct international networking. No unit or individual may establish or use other channels for international networking on their own. Those who violate the above provisions shall be ordered by the public security organ to stop networking, given a warning, and may also be fined not more than 15000 yuan; "If there are illegal gains, the illegal gains shall be confiscated.".
Therefore, in practice, many individuals and organizations who use Internet surfing software are subject to administrative penalties for unauthorized establishment and use of illegal channels for international networking. However, whether the "Regulations on the Administration of Network Data Security" will be prohibited or subject to administrative penalties after the official introduction depends on the specific provisions.
2、 Sorting out criminal cases involving individuals and organizations providing and selling advertising software to others
The author has searched for 52 cases of individuals and organizations providing and selling flipping software or VPN to others using "flipping software" or "VPN" as the search criteria. The author now makes a brief summary of the 52 cases that need to be focused on.
(1) Number of cases in recent years
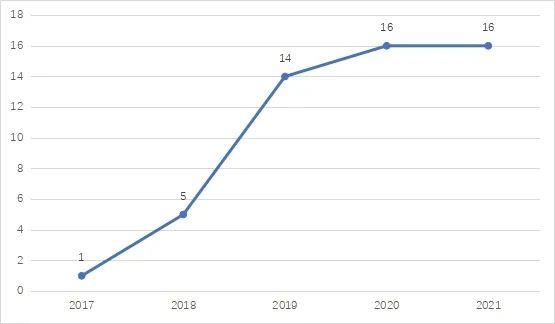
As can be seen from the table above, the number of crimes committed by this behavior has shown an upward trend in recent years, with the number remaining unchanged in 2020 and 2021.
(2) Different courts have different convictions for this act
In 52 cases, the courts have identified three types of crimes against the above-mentioned acts, as shown in the table below:
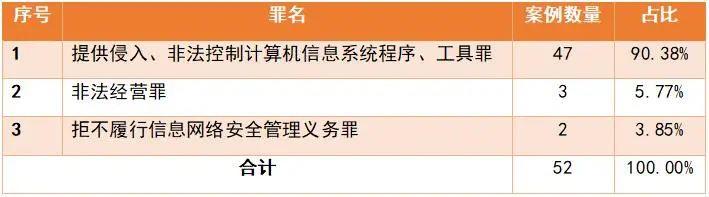
That is, the vast majority of courts believe that the act of providing and selling spyware to others constitutes the crime of providing intrusion or illegally controlling computer information system programs and tools, as defined in Article 285 (3) of the Criminal Law, while only a few courts believe that it constitutes the crime of illegal business operation or the crime of refusing to perform information network security management obligations.
Among the 52 cases, the author has found a case that can particularly illustrate that the nature of this act has been determined differently by the public prosecution law. In the (2018) E 1003 Xing Chu No. 150 case, the defendant established a network technology company, and later created a website to promote its agent sales and the VPN software it established and sold. After purchasing the software, users can access overseas Internet websites that cannot be accessed by domestic IP addresses. In order to seek illegal benefits, the defendant rented domestic and foreign servers and began to establish his own VPN platform to provide channels for others to sell online. In this case, the defendant was first detained for the crime of illegal business operations, and then arrested on suspicion of committing a crime of sabotaging a computer information system. The prosecution filed a public prosecution for the crime of providing intrusion and illegal control of computer information system programs and tools. Finally, the court ruled that the defendant constituted a crime of refusing to perform information network security management obligations.
(3) Distribution of involved amount/profit
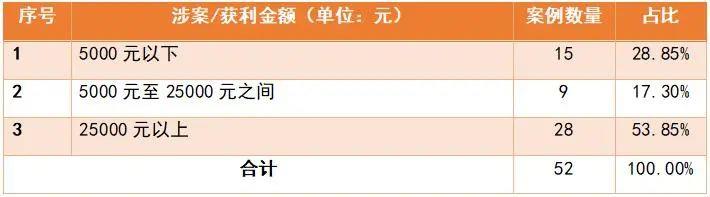
Given that the court has determined that the vast majority of the crimes of providing intrusion and illegal control of computer information system programs and tools are committed, we will temporarily analyze them according to the criminalization criteria for the illegal gains of this crime. According to Article 3 of the "Interpretation of the Supreme People's Court and the Supreme People's Procuratorate on Several Issues Concerning the Application of Law in Handling Criminal Cases that Threaten the Security of Computer Information Systems" (hereinafter referred to as the "Interpretation"), illegal gains of more than 5000 yuan are considered "serious circumstances.", "The circumstances are particularly serious if the amount is more than 25000 yuan. In 52 cases, the minimum profit is less than 1000 yuan, the maximum is nearly 2 million yuan, and the illegal income is more than 25000 yuan, accounting for 53.85%.".
(4) Judgment situation
Regarding the sentencing situation, first of all, each case is different. In terms of the circumstances of sentencing, some plead guilty to a crime, some constitute voluntary surrender, some have returned all or part of the illegal gains, and some have played different roles in joint crimes. This article only makes a single comparison between the amount of profits or illegal gains and the final judgment results, in order to let everyone understand the general direction of sentencing, The details are shown in the table below (a total of 90 people involved in 52 cases):
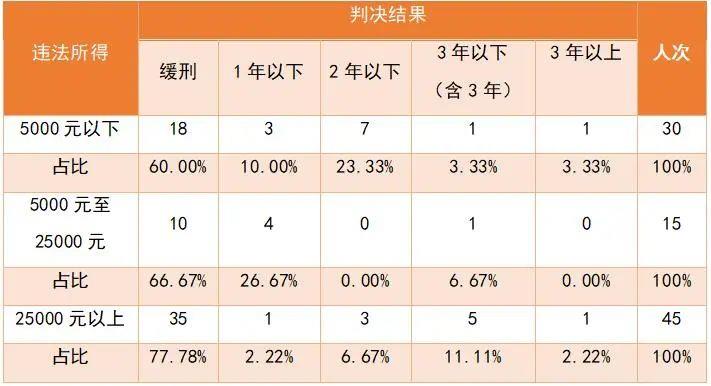
From the above table, it can be seen that most of the results of this case are suspended sentences, and even if the circumstances are "particularly serious" with a total amount of 25000 yuan or more, the majority of cases are suspended sentences. There were only two cases where the sentence was more than three years old, and both cases had a real sentence of three years and two months. From the perspective of most probation cases, there are circumstances of returning all illegal gains and pleading guilty to punishment.
3、 Main defense points
(1) Debate between Crime and Non crime
Although from a practical perspective, this act involves three charges, the author holds different views on whether it constitutes these three types of charges.
First, this act should not constitute the crime of providing intrusion or illegal control of computer information system programs or tools
Article 285 (3) of the Criminal Law: Whoever provides programs or tools specifically used to intrude into or illegally control computer information systems, or knowingly provides programs or tools to another person who commits an illegal or criminal act of intruding into or illegally controlling computer information systems, if the circumstances are serious, shall be punished in accordance with the provisions of the preceding paragraph. The crime of providing intrusion and illegal control of computer information system programs and tools stipulated in this article is a newly added crime in the Seventh Amendment to the Criminal Law. Article 2 of the Interpretation contains one of the following procedures and tools, It should be recognized as "a program or tool specifically used to intrude into or illegally control a computer information system" as stipulated in the third paragraph of Article 285 of the Criminal Law: (1) having the function of avoiding or breaking through the security protection measures of the computer information system and obtaining data from the computer information system without authorization or beyond authorization; (2) Having the function of avoiding or breaking through the security protection measures of computer information systems and exercising control over computer information systems without authorization or beyond authorization; (3) Other programs and tools specially designed to intrude, illegally control computer information systems, and illegally obtain data from computer information systems. Article 11: The terms "computer information system" and "computer system" as used in this interpretation refer to systems that have the function of automatically processing data, including computers, network equipment, communication equipment, automatic control equipment, etc.
In popular terms, "flipping" refers to bypassing China's legal regulations to browse the relevant webpage content of overseas servers, i.e. bypassing corresponding IP blockades, content filtering, domain name hijacking, traffic restrictions, etc., to achieve access to overseas network content. Therefore, whether the provided flipping software has the function of avoiding or breaking through the security protection measures of the computer information system to obtain system data and control the computer information system requires identification of the software. Only when the identification conclusion is that the software has the above functions can it constitute a crime, otherwise it should not be recognized as constituting this crime.
Second, this act should not constitute a crime of illegal business operations
The author found that in the case law, the court held that the reason for constituting the crime was that providing VPN or firewall software belonged to providing Internet virtual private network services and cross-border network access services. According to Article B13 of the "Telecommunication Service Classification Catalogue" attached to the "Telecommunications Regulations of the People's Republic of China", domestic Internet virtual private network service (ip-vpn) refers to the service that operators use their own or leased Internet network resources to customize the Internet closed user group network for domestic users using the TCP/IP protocol. The Internet virtual private network is mainly constructed using tcp/ip based technologies such as ip tunneling, and provides certain security and confidentiality. Encrypted transparent packet transmission can be achieved within the private network. B14 stipulates that Internet access service refers to the establishment of business nodes using access servers and corresponding software and hardware resources, and the use of public communication infrastructure to connect business nodes to the Internet backbone network, providing various users with Internet access services. Users can use public communication networks or other access means to connect to their business nodes and access the Internet through this node. The provision of Internet virtual private network services and cross-border network access services belongs to value-added telecommunications services. According to Article 7 of the Telecommunications Regulations of the People's Republic of China and Article 4 of the Measures for the Administration of Telecommunications Business Operation Licenses, operators of telecommunications services should obtain business licenses issued by telecommunications regulatory agencies in accordance with the law. Therefore, providing Internet virtual private network services and cross-border network access services without obtaining a business license belongs to unlicensed and illegal operations.
However, according to the crime of illegal business operation stipulated in Article 225 of the Criminal Law, the act of providing flipping software does not fall under the circumstances of the first three paragraphs, so does the act of providing flipping software fall under the proviso of the fourth paragraph? I don't think it belongs either. The reason is that in accordance with Article 71 of the Notice of the Ministry of Public Security of the Supreme People's Procuratorate on the Standards for the Filing and Prosecution of Criminal Cases under the Jurisdiction of Public Security Organs (2022) (hereinafter referred to as the "Standards for Filing and Prosecution"), there are a total of 12 illegal business activities that disrupt market order, including paragraph (6): renting international special lines, setting up private transfer equipment, or other methods, "Unauthorized operation of international telecommunications services or profit-making activities involving telecommunications services from Hong Kong, Macao, and Taiwan, disrupting the management order of the telecommunications market, under any of the following circumstances...". From the above provisions, it can be seen that international telecommunications business is to operate incoming and outgoing calls, and the act of providing information software is not to operate incoming and outgoing calls, nor is it to operate international telecommunications business. Article 71, paragraph 12, of the "Standards for Filing and Prosecuting Cases II" also refers to "engaging in other illegal business activities", but the Supreme Court clearly stated in the case of Wang Lijun's Unlicensed Corn Harvesting (Guiding Case No. 97) that the application of "other illegal business activities that seriously disrupt market order" stipulated in Article 225, paragraph 4, of the Criminal Law is applicable, A judgment should be made based on whether the relevant acts have social harmfulness, criminal illegality, and the necessity of criminal punishment commensurate with the illegal business operations specified in the first three items of Article 225 of the Criminal Law. To determine whether a business activity that violates relevant administrative regulations constitutes a crime of illegal business operations, consideration should be given to whether the business activity constitutes a serious disruption of market order. Business activities that violate relevant administrative regulations but have not seriously disrupted market order should not be recognized as the crime of illegal business operations. Article 3 of the "Notice of the Supreme People's Court on the Accurate Understanding and Application of the" National Provisions "in the Criminal Law": When trying cases of illegal business operations, people's courts at all levels must strictly grasp the scope of application of Article 225 (4) of the Criminal Law in accordance with the law. "If there is no clear provision in the relevant judicial interpretation as to whether the defendant's behavior belongs to the" other illegal business activities that seriously disrupt the market order "specified in Article 225 (4) of the Criminal Law, it shall be taken as a matter of legal application and submitted to the Supreme People's Court for instructions level by level.".
Therefore, whether the act of providing spyware belongs to "other illegal business activities that seriously disrupt the market order" in the crime of illegal business operations should be reported to the Supreme Court level by level. It is obviously inappropriate to directly criminalize and deal with the crime of illegal business operations without obtaining a positive response.
Third, this behavior should not constitute a crime of refusing to fulfill information network security management obligations
The crime of refusing to fulfill the obligation of information network security management is a newly added crime in the Criminal Law Amendment (9). Article 286-1 of the Criminal Law: If a network service provider fails to fulfill the obligations of information and network security management stipulated by laws and administrative regulations and refuses to take corrective measures upon the order of the regulatory department, and falls under any of the following circumstances, it shall be sentenced to fixed-term imprisonment of not more than three years, criminal detention, or public surveillance, and shall also, or shall only, be fined: (1) causing the massive dissemination of illegal information; (2) Causing the leakage of user information, causing serious consequences; (3) Causing the loss of evidence in a criminal case, and the circumstances are serious; (4) There are other serious circumstances.
The core element of this crime is to know who is a "network service provider"? According to Article 1 of the Interpretation of the Supreme People's Court and the Supreme People's Procuratorate on Several Issues Concerning the Application of Law to Criminal Cases such as Handling Illegal Use of Information Networks and Assistance in Information Network Criminal Activities, entities and individuals that provide the following services shall be recognized as "network service providers" as stipulated in Paragraph 1 of Article 286-1 of the Criminal Law: (1) network access, domain name registration and resolution, and other information network access, computing, storage Transmission services; (2) Information network application services such as information publishing, search engines, instant messaging, online payment, online reservation, online shopping, online games, online live streaming, website construction, security protection, advertising promotion, application stores, etc; (3) Utilize information networks to provide public services such as e-government, communications, energy, transportation, water conservancy, finance, education, and medical care. Secondly, if the regulatory authority orders to take corrective measures and refuses to make corrections, that is, if the regulatory authority does not order to make corrections and refuses to make corrections, it should not be treated as a criminal offence. Thirdly, it is necessary to achieve the degree of massive dissemination of illegal information, leakage of user information, loss of evidence, and serious consequences. Lei Jianbin of the Law and Industry Commission once mentioned that the obligations of network service providers refer to obligations related to network security, mainly including the security of information content, as well as the security of the information system itself. The fourth paragraph of the Criminal Law refers to other situations, which are of a bottomless nature and are equivalent in harm to the preceding three situations. It also includes endangering both the security of content and the security of the information network system itself. [Interpretation by the Law Working Committee of the Internet Provisions of the Criminal Law Amendment (IX)]
The author believes that providing Internet access software to others does not belong to the concept of a network service provider in the above provisions in essence. Providing Internet access software is only an extraterritorial access conducted on the basis of national legal channels, and does not belong to providing network access, let alone content that does not comply with other provisions. Therefore, it should not constitute a crime of refusing to perform information network security management obligations.
(2) Debate of Evidence
The Supreme People's Procuratorate issued the second batch of guiding cases in the 18th batch: Ye Yuanxing and Zhang Jianqiu provided programs for intruding into computer information systems, and Tan Fangmei illegally obtained data from computer information systems. In the case, it was clear that the review identified "programs specifically used for intruding into computer information systems," and generally required the public security organ to provide the following evidence: First, collect from the original storage media such as the seized and sealed computers and USB flash disks involved in the case Extract relevant electronic data. The second is a written record made after investigating and examining the involved procedures, the intruded computer information system, and electronic data. The third is documentary evidence that can confirm the technical principles, production purposes, functional uses, and operational effects of the procedures involved. The fourth is verbal evidence that the producer, provider, and user of the program involved have elaborated on the technical principles, production purposes, functional uses, and operating effects of the program, or audio-visual materials that can demonstrate the functions of the program involved. The fifth is evidence such as the technical principles and functions of the security protection measures of the intruded computer information system, as well as the testimony of professionals who can verify the consequences of the intrusion. Sixth, for those with operational conditions, the public security organ should be required to conduct investigation experiments. "If there is sufficient evidence to prove that the program involved is specifically designed to intrude into a computer information system or illegally obtain data from a computer information system, it can be directly recognized as a program specifically designed to intrude into a computer information system.".
During evidence review, it can be judged from the following aspects whether the involved program belongs to "programs specifically used to intrude into computer information systems": First, combining the security protection measures of the intruded computer information system, analyze whether the involved program has the purpose of intrusion, and whether it has the function of avoiding or breaking through the security protection measures of the computer information system. The second is to identify whether the program involved obtained computer information system data without authorization or beyond authorization based on the specific situation of computer information system intrusion. The third is to analyze whether the program involved belongs to a program "specifically" used to intrude into computer information systems.
According to Article 10 of the "Interpretation of the Supreme People's Court and the Supreme People's Procuratorate on Several Issues Concerning the Application of Law in Handling Criminal Cases that Threaten the Security of Computer Information Systems" and Article 17 of the "Provisions of the Supreme People's Court, the Supreme People's Procuratorate, and the Ministry of Public Security on Several Issues Concerning the Collection, Extraction, Examination, and Judgment of Electronic Data in Handling Criminal Cases", "If it is difficult to determine whether it belongs to a" program specifically used to intrude into computer information systems, "it is generally necessary to entrust a department responsible for the security protection and management of computer information systems at or above the provincial level to conduct an inspection. It may also be possible for a judicial appraisal institution to issue an appraisal opinion, or for an institution designated by the Ministry of Public Security to issue a report.".
In practice, it is important to focus on reviewing the judgment of inspection reports and expert opinions on the process and results of program operation, and combining the specific situation of the case to determine whether the program involved has the function of breaking through or avoiding computer information system security protection measures, and obtaining computer information system data without authorization or beyond authorization. In 52 cases, the vast majority of cases have authentication reports issued by authentication institutions on whether the software or VPN account links involved can directly access foreign websites that cannot be accessed by IP addresses in mainland China with the support of relevant software. "However, this report completely fails to meet the above evidentiary standards, and is not sufficient to conclude that the spyware belongs to a program specifically designed to intrude into computer information systems.". In addition to the appraisal conclusion, whether the qualifications of the appraisal institution and the appraisers meet the conditions can be used as defense points.
(3) Debate on Illegal Income
Article 3 of the Interpretation requires that the illegal gains constituting the crime of providing intrusion or illegal control of computer information system programs and tools should exceed 5000 yuan, while the illegal gains constituting the crime of illegal business operations require that the amount of illegal business operations be more than 50000 yuan or the illegal gains be more than 10000 yuan. What is "illegal gains"? Is it "total amount theory" or "net amount theory"? In response to this issue, the author found that the courts have not reached a unified determination. Article 64 of the Criminal Law only mentions that all property illegally obtained by criminals should be recovered or ordered to be refunded, but it does not provide the concept of illegal income. However, the concept of illegal gains is scattered in other relevant provisions. For example, Article 17 of the "Interpretation of the Supreme People's Court on Certain Issues Concerning the Specific Application of Law in the Trial of Criminal Cases of Illegal Publications": The term "operating amount" as used in this interpretation refers to the amount obtained by multiplying the pricing amount of illegal publications by the number of illegal publications operated by the perpetrator. The term "illegal income amount" as used in this interpretation refers to the amount of profits. Article 10 of the Interpretation of the Supreme People's Procuratorate on Several Issues Concerning the Specific Application of Law in Handling Criminal Cases of Insider Trading and Disclosure of Insider Information. The term "illegal gains" specified in Article 180, paragraph 1, of the Criminal Law refers to benefits obtained or losses avoided through insider trading. Article 4 of the "Interpretation of the Supreme People's Court and the Supreme People's Procuratorate on Several Issues Concerning the Specific Application of Law in Handling Criminal Cases of Infringement of Intellectual Property Rights": The amount of illegal business operations exceeds 200000 yuan or the amount of illegal gains exceeds 100000 yuan. It also distinguishes between the amount of business and illegal income. Another example is the "Notice on Printing and Distributing Typical Cases of Bribery Crimes", which mentioned in the bribery case of Wang Moumou in Jiangxi that it is necessary to accurately identify the illegal gains from bribery crimes and actively cooperate with the recovery of stolen goods and losses. In this case, the court adopted the balance of the acquisition amount paid by the actor minus the total asset value of the acquired enterprise at the time of acquisition and the evaluation value of the molybdenum mining rights involved to determine the illegal proceeds of bribery. That is, "illegal income" is mostly based on the "net amount theory".
In the 52 judgments mentioned above, the author found that there were various expressions in the court's determination of the amount, such as "amount involved", "profit amount", "illegal income", and "transfer amount". Only 8 judgments gave the amount involved and the profit amount respectively. Therefore, when defending, the defender should first look at the evidence. If the prosecution only provides data on total sales or income obtained through transfer, it can defend it using the term "net amount theory", and try to collect and submit evidence related to the case that reflects costs and expenses, such as the cost of self purchased search software
In short, individuals who use Flip Advisor software to browse overseas websites may be subject to administrative penalties at this stage, while providing and selling Flip Advisor software to others is extremely prone to criminal risks. When searching for relevant cases in this article, the author found that more often than not, they use social media software to engage in online fraud, disseminate obscene information, and conduct propaganda and education. The corresponding actions would constitute the crime of aiding trust, the crime of disseminating obscene materials, and the crime of using educational organizations to undermine the law. Therefore, we should not ignore the criminal issues caused by Flipping Software. It is everyone's responsibility to purify the network and maintain network information and data security.
Related recommendations
- Tax lawyers review the draft of the revised Tax Collection and Administration Law for soliciting opinions
- New Measures for Punishing "Dishonesty" by the Supreme People's Court at the Two Sessions in 2025 (Part 3): "Height Limit" Single Release Mechanism
- New Measures for Punishing "Dishonesty" by the Supreme People's Court at the Two Sessions in 2025 (Part 2): Grace Period System
- Interpretation of the Management Measures for Compliance Audit of Personal Information Protection - Feeling the Rhythm and Rhythm of Regulatory Flow